Your business website is your brand’s digital identity, and it needs to be just as secure as your physical location. Protecting customer data and ensuring compliance is important, especially when 60% of small businesses go under within 6 months of a cyber attack.
Whether launching your first website or managing a long-established online hub, the stakes have never been higher. It’s time to turn your website into the secure, compliant, customer-centric digital fortress your operation deserves.
This blog will share the essential elements for building a safe and reliable website that keeps your sensitive information locked down tight. From implementing powerful encryption to navigating tricky compliance rules, you will learn practical strategies to strengthen your online presence and keep your customers’ trust.
Why Website Security and Compliance Matter for Businesses
An ounce of prevention is worth a pound of cure, especially when it comes to website security and compliance. Protecting your website from cyber threats safeguards your business from data breaches that can harm customer trust and lead to expensive legal trouble. Compliance isn’t just about ticking boxes; it’s about showing customers that their privacy is a priority.
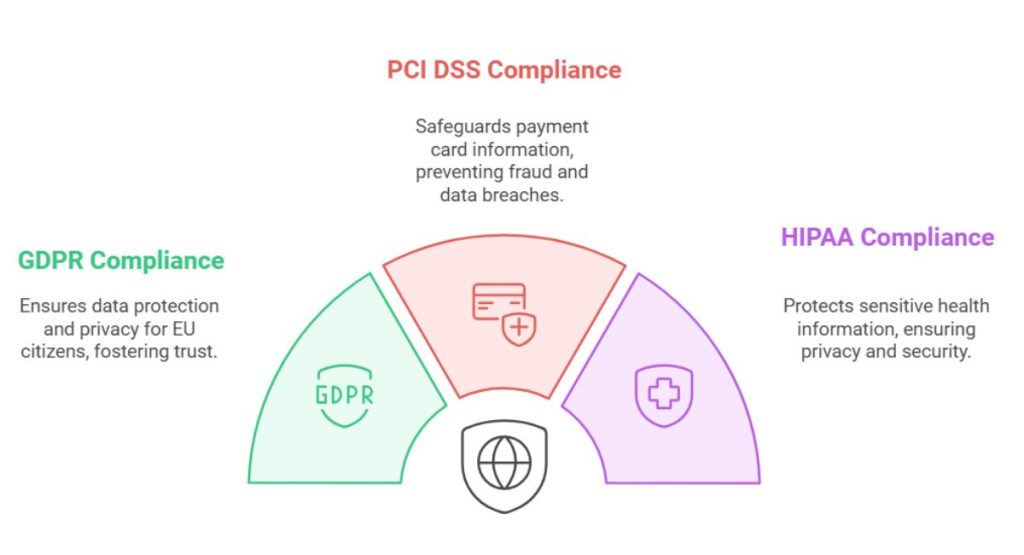
Meeting standards like these can protect your business and build loyalty:
- GDPR (General Data Protection Regulation)
- PCI DSS (Payment Card Industry Data Security Standard)
- HIPAA (Health Insurance Portability and Accountability Act)
These standards help ensure your website is safe and trustworthy, reducing risks and enhancing customer confidence. Prioritizing security and compliance shows your commitment to protecting users every step of the way.
Expert Team
Key Elements of a Secure Business Website
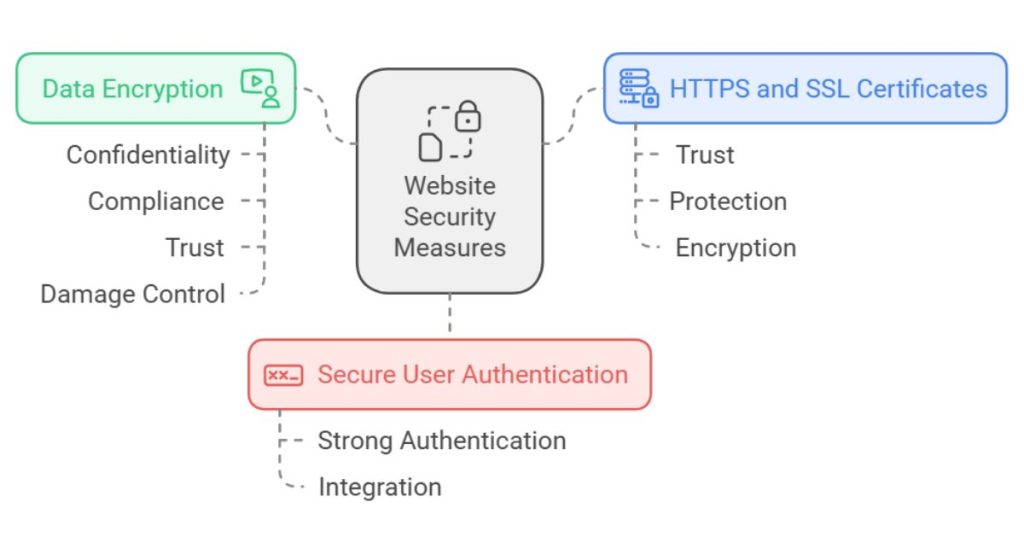
Better be safe than sorry especially when it comes to your website’s security. Key features like SSL encryption protect data, while regular security audits identify risks early. Strong password policies, two-factor authentication, reliable hosting, and firewalls add layers of defense against cyber threats.
Regular backups prevent data loss, and compliance with privacy laws, like GDPR, builds trust. Together, these elements keep your site secure, reassure your customers, and strengthen your brand’s reputation for reliability.
1. HTTPS and SSL Certificates
Using HTTPS with SSL certificates is crucial for protecting data as it moves between users and your website. Notably, a 2022 survey by DigiCert revealed that 89% of internet users are more likely to trust websites displaying security indicators like HTTPS.
This makes SSL essential for building trust and protecting user information. HTTPS encrypts sensitive information, like passwords and payment details, making it extremely difficult for hackers to intercept. The SSL “lock” icon in the browser reassures users that their data is safe.
2. Data Encryption for Sensitive Information
When it comes to your business website, keeping sensitive information like passwords, customer data, and payment details locked down tight is an absolute must. That’s where data encryption comes in, it’s the process of scrambling information so that only authorized parties can access it.
But why is encryption so important?
- Confidentiality: Encrypted data is meaningless to anyone without the right “key.”
- Compliance: Encryption helps you meet data protection regulations.
- Trust: Customers feel safe knowing their info is secure on your site.
- Damage Control: Stolen encrypted data is useless to attackers.
Data encryption is an absolute must when it comes to safeguarding your business. It’s the foundation of a truly secure website that protects your information and customers.
3. Secure User Authentication and Authorization
Implementing secure login systems is key to protecting user accounts and sensitive data. Strong user authentication methods, like two-factor authentication (2FA), add an extra layer of security by requiring both a password and a second form of verification. Integrating these security features into the web development process ensures that security is prioritized.
Strong password policies and regular updates make accounts harder to breach. Role-based access control (RBAC) is another important step, as it limits access to sensitive information based on each user’s role, ensuring that only authorized individuals can reach specific data or functions.
Building Compliance into Your Business Website
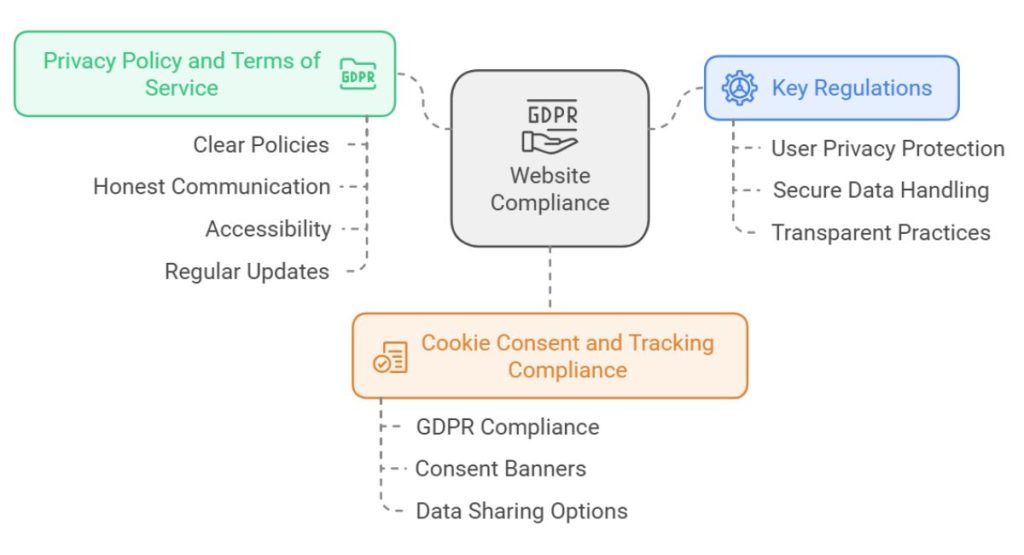
Want to keep your website on the right side of the law? Start by protecting user data and making your site accessible to everyone. Just need to clear the cookie notices, straightforward privacy policies, and secure ways to handle sensitive information.
Remember to run regular checks to ensure you’re following all the rules. Good compliance isn’t just about avoiding legal trouble; it’s about building trust with your visitors.
1. Understanding Key Compliance Regulations
Keeping up with website regulations might seem overwhelming, but it’s simpler than you think! These rules protect both your business and your users. These regulations help protect users’ privacy, ensuring companies handle data securely and transparently. For any business website, following these rules isn’t just about avoiding fines it’s about building trust with users.
Here’s a quick overview:
- GDPR: EU law that mandates strict guidelines on data collection, processing, and sharing.
- CCPA: California’s data privacy law, focuses on consumer rights over personal information.
- HIPAA: U.S. law protecting medical data, mainly for healthcare providers.
Benefits of Compliance:
- Builds customer trust by showing a commitment to data privacy.
- Enhances security measures, reducing data breach risks.
- Helps avoid hefty fines and legal penalties.
2. Setting Up a Privacy Policy and Terms of Service
Privacy policy and terms of service are like your website’s rulebook. They tell visitors exactly how you will handle their information and what they can expect when using your site. Clear, honest policies aren’t just good practice, they are essential for building trust and staying legal.
Keep your policies simple, accessible, and up-to-date.
Digital Privacy Expert Sarah Chen, says “A well-crafted privacy policy isn’t just about legal compliance. It’s a powerful trust signal that shows your commitment to protecting user data. When customers understand how their information is being used, they’re more likely to engage with your business.”
3. Cookie Consent and Tracking Compliance
Managing cookie consent and tracking compliance is vital for websites under regulations like GDPR. Websites must inform users about cookies and tracking tools that collect data, usually through consent banners. These banners let users decide which types of data they’re comfortable sharing, creating a more transparent online experience.
As per one survey by the Pew Research Center, 79% of Americans are concerned about how companies use the data collected through their website cookies. Setting up consent options not only keeps you compliant but also respects user preferences, building trust and enhancing your brand’s credibility.
Implementing Strong Cybersecurity Practices
An ounce of prevention is worth a pound of cure when it comes to cybersecurity. Strong practices like multi-factor authentication, data encryption, and firewalls build a solid defense against digital threats.
Regular software updates and access controls further protect against vulnerabilities, while employee training keeps everyone alert to risks. Monitoring for suspicious activity and maintaining secure data backups, your business is well-prepared to respond and recover quickly, safeguarding your data and reputation.
1. Regular Security Audits and Vulnerability Testing
We all know that forewarned is forearmed; that’s what regular security audits and vulnerability testing help businesses stay ahead of potential cyber threats. When planning a budget for website development, it’s smart to allocate funds specifically for ongoing security audits because these assessments reveal weaknesses that could be exploited, allowing you to fix them before issues occur.
Security audits provide a comprehensive overview of your system’s defenses, while vulnerability testing, like penetration testing, simulates attacks to identify critical gaps. By scheduling these evaluations regularly, you strengthen your cybersecurity posture and protect your business from potential risks.
2. Firewall and Web Application Security
Don’t leave your website’s security up to chance put a firewall in place to keep the bad guys out. Think of it as your site’s bodyguard, filtering traffic and blocking potential threats like hacking attempts or malware. Web application firewalls (WAFs) are especially useful for this task, scanning incoming data and shutting down suspicious activity.
According to a Verizon report, 43% of cyberattacks target small businesses, making firewalls essential. Set up your firewall to block suspicious IP addresses, limit access to sensitive areas, and inspect incoming data. Don’t neglect your firewall – it’s a simple way to beef up your website’s protection.
3. Malware Detection and Intrusion Prevention
A good rule of thumb is always to follow, prevention beats recovery every time. Protecting your website from malware and unauthorized access is essential for keeping data secure and user trust intact. Malware detection and intrusion prevention systems (IPS) play a vital role in identifying and blocking these threats in real-time, stopping attacks before they cause harm.
Here’s why these tools are important:
- Unauthorized Access Prevention: Blocks attempts to access sensitive areas, protecting data and user information.
- Real-time Scanning: Constantly scans for suspicious files or activity, catching threats before they spread.
- Mitigating Harm: Reduces the risk of severe damage by intercepting malware and intrusions early.
- Threat Analysis: Analyzes potential risks, helping you respond to emerging threats quickly.
Data Protection Best Practices for Business Websites
Keeping customer data safe is crucial for building trust and staying on the right side of the law. Start with encryption and use SSL to secure data transfers. Then, follow privacy rules like GDPR and CCPA, collect only what you need, and store everything safely.
Don’t forget to give users control over their info and be upfront about your data practices. Staying on top of security keeps your website and business protected.
1. Regular Backups and Disaster Recovery Plans
Backing up your data regularly and having a disaster recovery plan is essential for keeping your business running smoothly, even in the face of unexpected data loss or a security breach. Automated backups and secure, redundant storage solutions ensure that important information can be quickly recovered, minimizing downtime and protecting your business from major disruptions.
One of the top cybersecurity experts Alan Calder, says “A good disaster recovery plan is a lifeline for business continuity when data loss threatens your operations.” By planning for continuity, businesses can confidently manage potential risks, safeguarding both data and reputation.
2. Data Minimization and Access Restrictions
Limiting data exposure is key to protecting sensitive information. Data minimization techniques help by collecting only the absolutely necessary data, while access restrictions ensure that only authorized users can view or handle it.
Businesses should follow the principle of least privilege, limiting access to sensitive data based on roles, and reducing potential risks. Setting data retention limits and restricting access to essential personnel strengthens information privacy and helps keep valuable data secure.
3. Educating Employees on Cybersecurity Best Practices
Training employees on cybersecurity best practices is essential to keeping your business safe from cyber threats. With proper training, staff can recognize phishing attempts, use secure password practices, and handle data responsibly.
A report by IBM (Cost of a Data Breach Report), found that human error contributes to 95% of cybersecurity breaches, highlighting the importance of awareness. Educating employees on security protocols empowers them to spot threats early, follow safe data-handling procedures, and actively protect sensitive company information from potential attacks.
Managing Third-Party Integrations and Data Sharing
Bringing in outside tools and services can be super helpful, but you have to keep a close eye on data security. Start by assessing vendor security and setting clear data-sharing agreements to outline how information is protected.
Regular audits help ensure third parties handle data responsibly. Use secure APIs and encryption for data transfers, and limit third-party access to only what’s necessary. Staying up-to-date on regulatory requirements and integration updates keeps your data protection strong and compliant.
1. Vetting Third-Party Vendors for Security Compliance
Evaluating third-party vendors for security compliance is crucial to safeguarding your business’s data. Start by assessing each vendor’s security standards and conducting regular audits to identify any risks in data-sharing practices. This process ensures that all third parties align with your security and privacy needs.
However investing in custom web development services gives you a personalized approach that incorporates security checks and ensures third-party integrations are compliant, keeping data safe while enhancing business functionality.
2. Managing API Security for Integrated Applications
Securing APIs is crucial for protecting data shared with third-party applications on business websites. Key practices include strong authentication for each request, encrypted connections to safeguard data, and rate limiting to prevent misuse. These steps add vital layers of security, reducing vulnerabilities in your integration.
Regular API monitoring is also essential to detect and respond to suspicious activity quickly. As cybersecurity expert Troy Hunt puts it, “APIs are the backbone of modern web applications, so securing them is critical to maintaining data integrity and privacy.” By prioritizing API security, businesses can ensure their integrations remain safe, reliable, and compliant.
Monitoring and Responding to Security Incidents
Don’t wait for a breach to happen stay one step ahead with 24/7 security monitoring. Use smart tools to spot threats fast, and have a clear incident response plan ready to go.
When things go wrong, quickly contain the damage, communicate with stakeholders, and investigate what went wrong. With the right preparation and training, your team can tackle security incidents like pros.
1. Setting Up an Incident Response Plan
Hope for the best, but prepare for the worst! An incident response protocol lays out the steps your team should take to quickly identify, contain, and mitigate any threats. This prep work is crucial because a 2023 IBM study found that companies with a well-rehearsed incident response plan save an average of $2.66 million per breach compared to those without.
Create a clear, step-by-step action plan detailing who does what when a breach is detected. Include procedures for isolating impacted systems, recovering data, and communicating with stakeholders. With the right response in place, you can minimize downtime, protect sensitive information, and get your website back on track fast.
2. Using Monitoring Tools for Threat Detection
Real-time monitoring tools, like SIEM (Security Information and Event Management) systems, are essential for catching and responding to security threats as they happen. These tools provide continuous monitoring, automated alerts, and quick analysis, helping companies prevent potential breaches.
Some effective monitoring tools include:
- SIEM Software: Aggregates and analyzes security data to flag threats.
- Log Management Tools: Stores and reviews log data for suspicious patterns.
- Intrusion Detection Systems (IDS): Identifies unusual activities in network traffic.
- Endpoint Detection and Response (EDR): Monitors endpoint devices for threats.
Conclusion
Creating a secure, compliant business website requires careful planning. Key steps include SSL encryption, access controls, and regular backups to protect data. Employee training and monitoring tools help your team stay ahead of threats.
Compliance is equally important. Following regulations like GDPR and setting clear data-sharing policies help protect user privacy and build trust. A secure, compliant site not only protects data but also strengthens your business’s reputation.
But if you are looking for a trusted partner for building a secure website then Softnix is the name you can trust with extensive experience in web development services, security, and compliance. Choosing Softnix means investing in expert practices and a team dedicated to creating safe, reliable websites tailored to your business needs.
FAQs about Building a Secure Website
What are the basic steps to secure a business website?
To secure your business website, implement SSL certificates for encrypted connections, enforce strong password policies, regularly update software, use firewalls, conduct frequent security audits, and back up data consistently. These measures help protect against cyber threats and data breaches.
How do SSL certificates protect data on websites?
SSL certificates encrypt data exchanged between a user’s browser and your website, ensuring sensitive information like passwords and credit card numbers remain private and secure from interception. This encryption builds trust and protects user data.
What compliance regulations should business websites follow?
Business websites should adhere to regulations such as GDPR for data protection, PCI DSS for payment security, and HIPAA for healthcare information. Compliance ensures legal operation and builds customer trust by safeguarding personal information.
How does HTTPS differ from HTTP for website security?
HTTPS is the secure version of HTTP, using SSL/TLS protocols to encrypt data between the browser and server. This encryption prevents unauthorized access, protects sensitive information, and enhances user trust.
What are the best practices for data encryption on a website?
Use strong encryption algorithms, implement SSL/TLS certificates, encrypt sensitive data at rest and in transit, and regularly update encryption protocols. These practices ensure data remains confidential and secure from unauthorized access.
How can I make my login system more secure?
Enhance login security by enforcing strong, unique passwords, implementing multi-factor authentication (MFA), limiting login attempts, and regularly updating authentication protocols. These steps reduce the risk of unauthorized access.
What is the importance of a privacy policy on a website?
A privacy policy informs users about how their data is collected, used, and protected. It demonstrates transparency, builds trust, and ensures compliance with data protection laws, fostering a trustworthy relationship with users.
How can I protect my website from malware?
Protect your website by installing security plugins, conducting regular malware scans, keeping software updated, using firewalls, and educating staff about phishing attacks. These measures help prevent malware infections and maintain site integrity.
What does GDPR compliance mean for business websites?
GDPR compliance requires websites to protect EU users’ data, obtain explicit consent for data collection, allow data access and deletion upon request, and report data breaches promptly. Compliance avoids legal penalties and builds user trust.
How often should I run security audits on my website?
Conduct security audits at least quarterly, or more frequently if your website handles sensitive data or undergoes regular updates. Regular audits help identify vulnerabilities and ensure ongoing protection against threats.
What is a web application firewall (WAF) and do I need one?
WAF filters and monitors incoming traffic to protect your website from malicious activities like SQL injections and cross-site scripting. Implementing a WAF enhances security by blocking harmful requests before they reach your site.
How do cookies and tracking affect compliance?
Cookies and tracking collect user data, which must be managed in compliance with regulations like GDPR. Inform users about data collection, obtain consent, and provide options to manage preferences to ensure legal compliance and maintain trust.
What should be included in a website’s incident response plan?
An incident response plan should outline procedures for identifying, containing, eradicating, and recovering from security breaches. Include roles and responsibilities, communication strategies, and post-incident analysis to improve future responses.
How do I choose a secure third-party vendor for my site?
Select vendors with strong security practices, compliance certifications, and positive reputations. Conduct thorough assessments, review security policies, and ensure they align with your security standards to protect your website and data.
Why should I consider Softnix for secure website development?
Softnix specializes in creating secure, compliant websites tailored to your business needs. With expertise in advanced security measures and regulatory adherence, Softnix ensures your website is robust, reliable, and trustworthy, safeguarding your online presence.